Defensible Deletion: The Law & The Promise

The Goal
Defensible deletion is a first cousin to Proportionality. Both procedural rules intend to maximize relevant data responsiveness for litigation, and according to Defensible Deletion Strategy: Getting Rid of Your Unnecessary Data (https://www.specialcounsel.com/):
- Defensible deletion is a comprehensive approach to reduce the storage costs and legal risks associated with the retention of electronically stored information.
The Law
Defensible deletion is methodically deleting electronically stored information (ESI) when no longer useful. Courts are clear that deletion of material, which is not presently under a legal hold nor required for a statutory or business purpose can, and should, be deleted. Under the Federal Rules of Civil Procedure (FRCP), courts may not grant sanctions when a party to litigation defensibly deletes data prior to the attachment of a preservation obligation. Per FRCP 37(e):
- Absent exceptional circumstances, a court may not impose sanctions under these rules on a party for failing to provide electronically stored information lost because of the routine, good-faith operation of an electronic information system.
And, amendments to the FRCP reinforce defensible deletion by supporting proportionality in preservation.
The Defensible Data Strategy
Defining a reasonable deletion strategy requires knowing what information the organization has, and where it is stored. The strategy objectives are:
- have confidence in what data to keep, archive or delete
- avoid court sanctions
- eliminate ESI that has no value
The Data Dichotomy – Enabler & Inhibitor
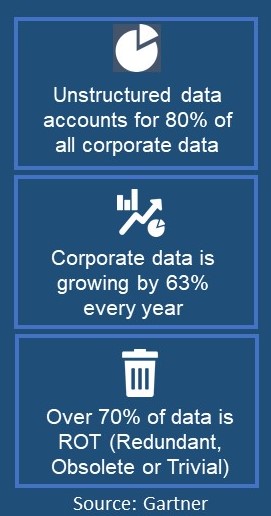
Achieving a deletion strategy is not straightforward. Unstructured data holds relevant and responsive data, but it is unmanaged, untethered, and roaming loose across the enterprise. Emails, attachments, and thousands of files on countless endpoints contribute to the increasing ocean of data. Unstructured data is home to Personally Identifiable Information risk (PII/PHI/PCI). According to Iron Mountain, of companies responding to a survey:
• 56% – cannot separate data eligible to delete from legal holds
• 50% – over-preserve emails and ESI
• 61% – do not regularly delete eligible data
• 78% – cannot locate ESI when needed
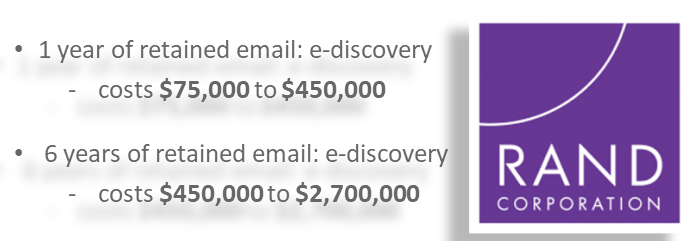
RAND Corporation highlights one case with ten (10) custodians. Quick math demonstrates the exponential increase in cost of retaining unstructured data. In this scenario, the increase reflects as much as 3600%.
The Recap
The evidence is clear – defensible deletion and proportionality hold the promise for streamlined litigation response, safer data, reduced costs, and litigation strategy with higher confidence. But, unstructured data is both the source of delivering on the promise and the obstacle to realizing the promise.
Realizing the Promise of Defensible Deletion (& Proportionality)
Effectively achieving defensible deletion requires:
- A repeatable data mapping audit
- A streamlined and efficient legal hold policy
- Processes to disposition/delete documents in accordance with data retention and data governance principles
- Documentation of disposition actions
In conjunction with legal hold, Heureka enables defensible deletion and proportionality (see “Proportionality” blog: Proportionality-Mitigating Costly Over-Discovery
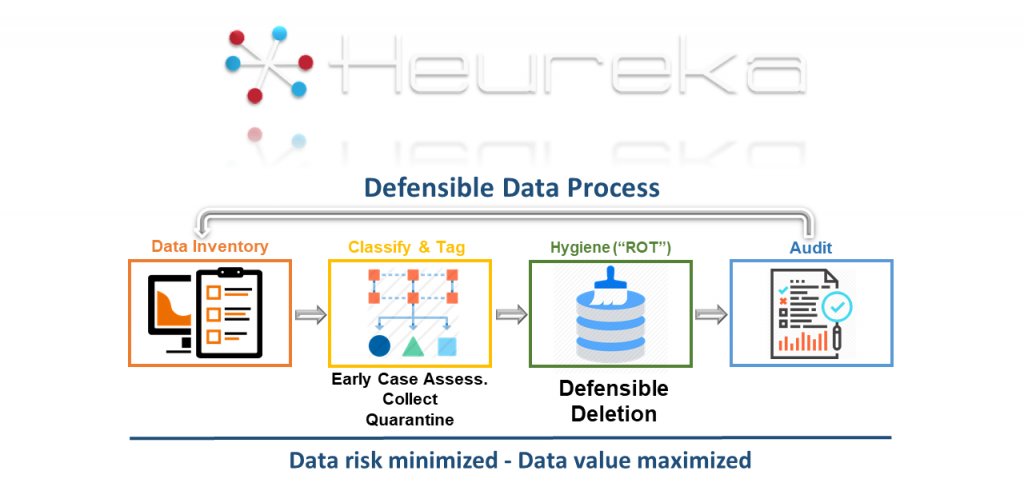
Heureka identifies, indexes, and classifies unstructured data and allows file actions to include quarantine, delete, collect, and encrypt. No data is moved or copied, ensuring adherence to Governance, and eliminating the risk of propagating PII across the network.
We would appreciate the opportunity to demonstrate our capabiities. Please feel free to schedule a demo