Hackers Are Gunning for Unstructured Data

PwC’s report shines light on why hackers are gunning for unstructured data…
49% (9,500 respondents) do not have an accurate inventory of personal data (PwC)
The Wall Street Journal: Survey Roundup: Many Companies Falling Short on Infosec (PwC)
https://www.wsj.com/articles/survey-roundup-many-companies-falling-short-on-infosec-training-1521555558?tesla=y
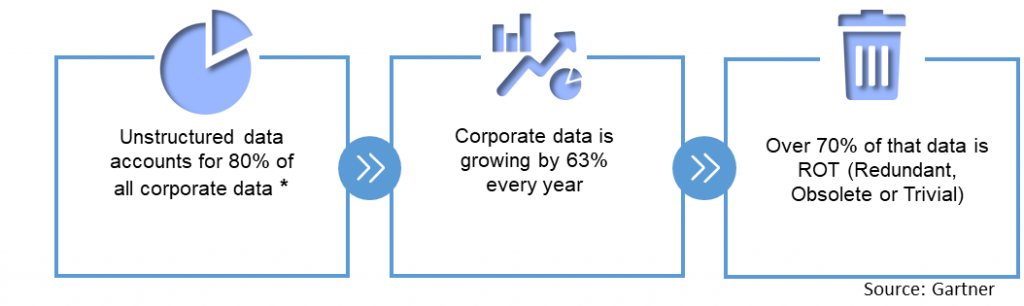
A large remote workforce has further stressed a secure perimeter for many organizations and hackers have found new ways to infiltrate enterprises, seeking data that is roaming wild and untethered: unstructured data. Unstructured data poses a large attack surface and much of unstructured data is “structured” data repurposed for everyday use. Unstructured data is 80% of all data and growing exponentially.
Having data spread across multiple tiers of applications and cloud services, and sometimes out on unauthorized services, “has greatly impacted the CISO’s ability to have unified visibility,” says Greg Jensen, senior principal director of cloud security at Oracle. “Hidden in the mounds of security data across every enterprise could be the fingerprints and tell-tell signs of an attack,” Jensen says. But only 16% of CISOs are able to collect, analyze, and respond to 75% or more of their security event telemetry.
Good News, and a Little Bad News
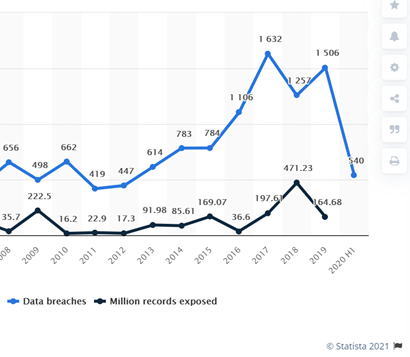
Statista reports a decrease in the number of breaches from 2019 to 2020. Conversely, The Ponemon Institute reports the cost of a breach is up a tick. The average cost of a data breach in the US in 2020 was $8.64M, up from $8.19M in 2019. Organizations who lacked security automation and incident response mechanisms experienced a higher cost of remediation. It often takes six (6) months to discover a breach.
Some Bear More Risk Than Others
Those enterprises most at risk are those that are disruptive, commanding their markets by moving data to the edges to serve customers. The increased market share and revenue are weighted against the increased probability of data breaches.
Gain Control of Unstructured Data: The Benefits
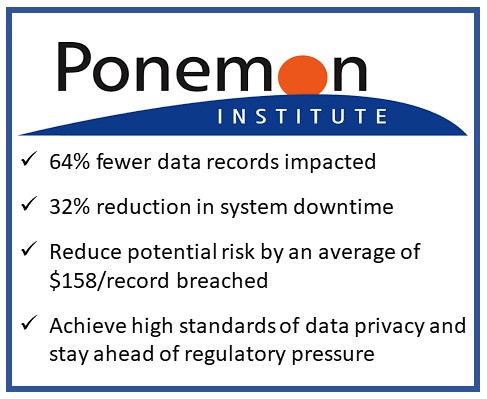
Data compliance is good for all. Heureka’s Intelligence Platform is the only tool to find and remediate redundant, obsolete, sensitive and trivial data at rest and in place, with minimal impact on infrastructure. Heureka’s automatic risk detection enables data governance and compliance with features to cleanse data by deleting and quarantining files that pose risk. The Heureka Intelligence platform provides hands-off, automated endpoint sweep for personally identifiable information (PII) and even offensive language.
Gain Control of Unstructured Data: The How
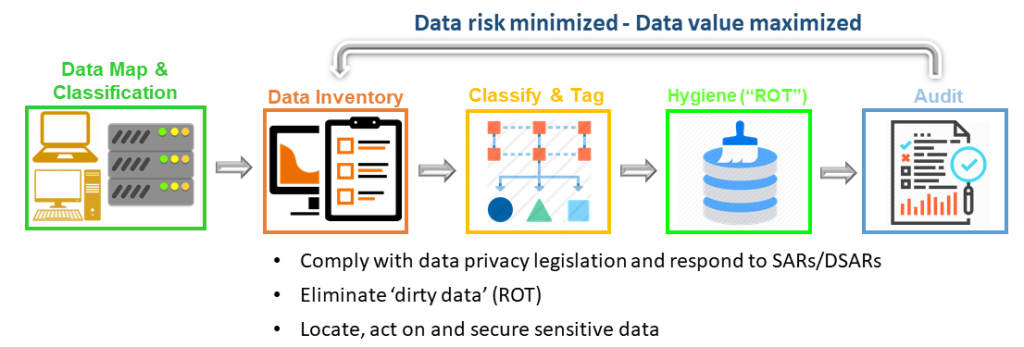
We would appreciate the opportunity to show you the how. Please schedule a demonstration at your convenience.
hackers gunning for unstructured data