Unstructured Data Risk – What Experts Say
The danger of unstructured data
According to PandaSecurity.com: Unstructured data makes compliance with (data privacy) difficult because it is not easily organized or processed.
The big (unstructured) data problem
Forbes, Juliette Rizkallah, Forbes Councils Member – Forbes Technology Council. Right now, enterprises are woefully unprepared. Nearly 80% of enterprises have very little visibility into what’s happening across their unstructured data, let alone how to manage it. Enterprises are simply not ready to protect data in this form because they don’t understand just how much they have. Worse yet, they don’t even know what lies within those unstructured data files or who owns these files. Based on a recent survey created by my company, as many as 71% of enterprises are struggling with how to manage and protect unstructured data.
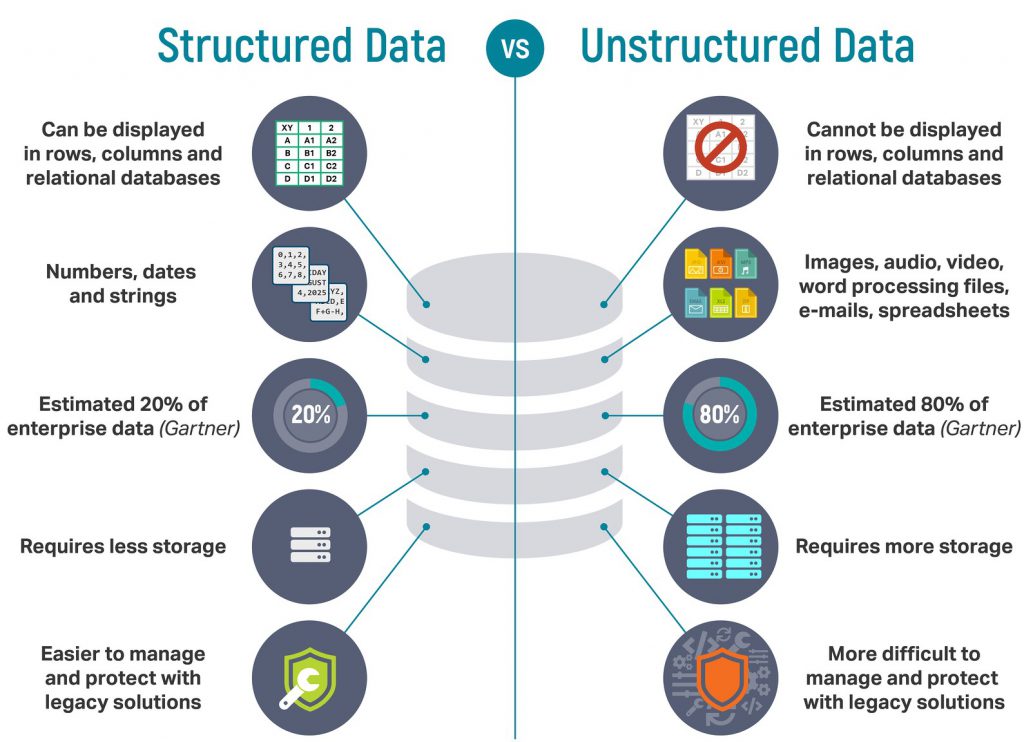
Risk levels of structured versus unstructured data
SecurityIntelligence.com, Paula Musich: from Data Risk Management, Part 3: Assessing Risk Levels of Structured Versus Unstructured Data
Unstructured Data Is an Easy Target – Cybercriminals are aware that critical unstructured data is a much easier target for theft than structured data protected by corporate firewalls, identity and access controls, encryption, and database activity monitoring. Organizations struggle to understand where critical unstructured data is, how it is used and who has access to it, so it represents a bigger risk to the enterprise.
Why unstructured data is putting your organization at risk
The SHI Blog blog.shi.com, SHI Staff: Herein lies the problem with unstructured data: Managing it is an extremely costly endeavor. You’re likely spending a lot of money to store files that are obsolete or duplicates.

Gartner Research estimates that it costs $5 million annually to manage 1 petabyte of data.
Unstructured data compliance: obstacles and solutions
ComputerWeekly.com, Stephen Pritchard. “Stored unstructured data could be a black hole full of unknown risk.” says Neil Harris, head of technical services at law firm DWF. “Data retention is a key one: you are likely to have some data for longer than you should.”
This “data debt”, he suggests, is unlikely to attract regulatory penalties, unless the data is lost or stolen. “If you don’t know what you have or where it is, you can’t protect it,” he warns.
Unstructured data: the threat you cannot see
DarkReading.com, Charles Fullwood: Unstructured Data: The Threat You Cannot See – Why security teams needs to take a cognitive approach to the increasing volumes of data flowing from sources they don’t control.
By 2022, 93% of all data will be unstructured. Traditional security focuses on mitigating external threats — perimeter defenses to ward off the bad guys. As such, we often focus our security strategies on firewalls, antivirus software, and secure passwords. Security innovation has almost always had this perimeter philosophy at its core. However, a myopic focus on perimeter protection severely limits the overall security strategy, potentially rendering it ineffective without complementary, proactive measures in place.
Don’t forget content in your data privacy strategy
DATAVERSITY, Kyle McNabb: Most (organizations) have neglected to account for unstructured data and content. With the explosive growth of records and the widespread remote workforce, there is a vast volume of unstructured data living in documents and records. If organizations continue to leave unstructured data out of privacy efforts, then organizations will not only fail to comply, but also struggle to thrive – even survive – in the post-pandemic, digital world.
According to a 2020 AIIM study, the amount of information coming into organizations will increase up to 4.5 times in the next 18 to 24 months – and 60 percent of that data will be unstructured.
https://www.dataversity.net/dont-forget-content-in-your-data-privacy-strategy/
The truth about unstructured data
According to SecurityMagazine.com, Deborah Kish: The first step is discovery, using a scanning process to analyze file information across enterprise files, discovering unprotected files and looking for sensitive information. https://www.securitymagazine.com/articles/90606-the-truth-about-unstructured-data
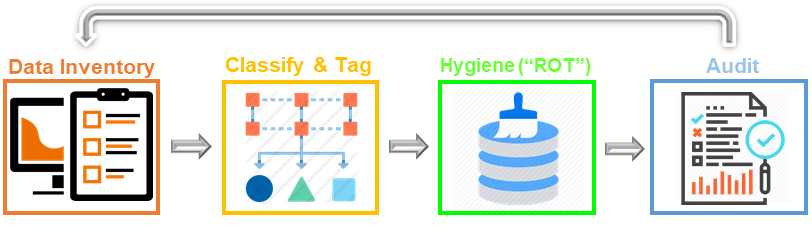
Heureka’s platform enables unstructured data compliance
- Discovery/Inventory – Map, index, classify & tag unstructured data by context, file type and date
- Data Retention Enforcement – files can now be dispositioned based on file create and/or modified date
- Defensible Data Deletion – Classification tags assigned to each file indicate retention or file disposal.
- DSARs & Breach Management – supporting and enabling DSAR management and breach response workflows
We appreciate the opportunity to give you a tour. Schedule a demo below.
Unstructured Data Risk – What Experts Say
Unstructured Data Risk – What Experts Say